The module didmos Federation Services is a toolkit specifically designed for federated IAM environments. This kind of environment often presents with its own unique challenges such as a high number of IdPs or non-web authentication. Especially the latter is not only an important subject matter for research infrastructures. didmos Federation Services will continuously be amended by new tools to ensure to address the latest issues. Moreover, this toolkit will also help to improve functionality and efficiency for SSO, which in turn increases the security of the IT infrastructure. In order for this to be successful, the input of the community is invaluable.
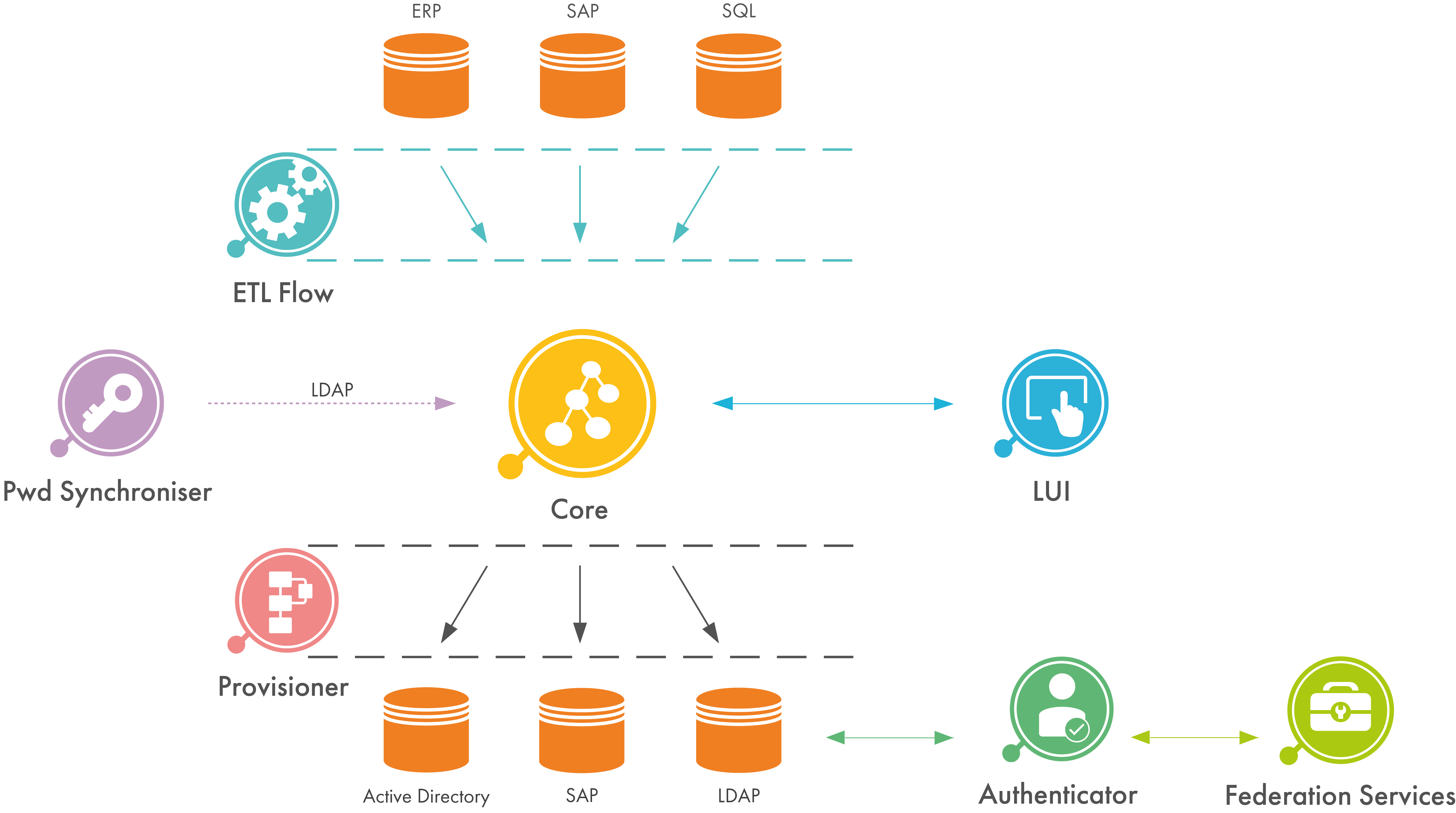
didmos Federation Services

Federation Services
Tools
Each tool is designed in a way to allow them to seamlessly work with didmos modules, such as didmos Authenticator but can also be used as a stand-alone solution.
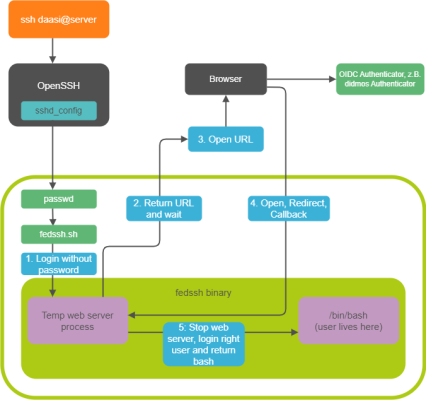
The first tool of the didmos Federation Services is FedSSH.
FedSSH
FedSSH is a tool which connects SSH access to servers with web-based, federated SSO authentication.
By default, SSH uses a password or a public key for authentication. Usually, both options will require local user and credential management, which can become problematic. Users who are supposed to access the server need to be known within the respective organisation, and accordingly these users need to be created on the server to be accessed. By contrast federated IAM assumes all users within the federation to have permission to access resources due to the special trust established within the federation. As a side effect the SSH login can consequently be connected to the central IdP via SSO.
Especially in scenarios which require access to multiple servers and/or virtual environments FedSSH allows for an improved user experience and makes it easier to administrate. By connecting an IdP such as didmos Authenticator or Shibboleth, users only have to login once, hence they also only need to remember a single password. For administrators, this means less forgotten passwords and easier account management. For instance, if a user leaves an organisation it is only necessary to disable one account in order to ensure all connected servers can no longer be accessed by this user.
FedSSH can be installed on Unix servers and be integrated into existing SSH configurations. A major advantage of the solution is that no additional software is required on the client side. Any given SSH client can be used without further modification. When the connection is established via SSH a temporary web server is created which serves as an OpenID Connect (OIDC) client. The user receives a short-lived link which is called up in a browser, and is forwarded to the IdP via OIDC. There, the login can take place (if the user did not yet login at another application within the SSO network), and the attributes are transferred to FedSSH web server. Via the unique user name, FedSSH can match the user to existing users on the server or dynamically create one, depending on the configuration. Further attributes, such as group memberships or eduPersonEntitlement, can be used for authorisation. The roadmap includes an alternate flow using the SAML2 protocol (instead of OIDC).