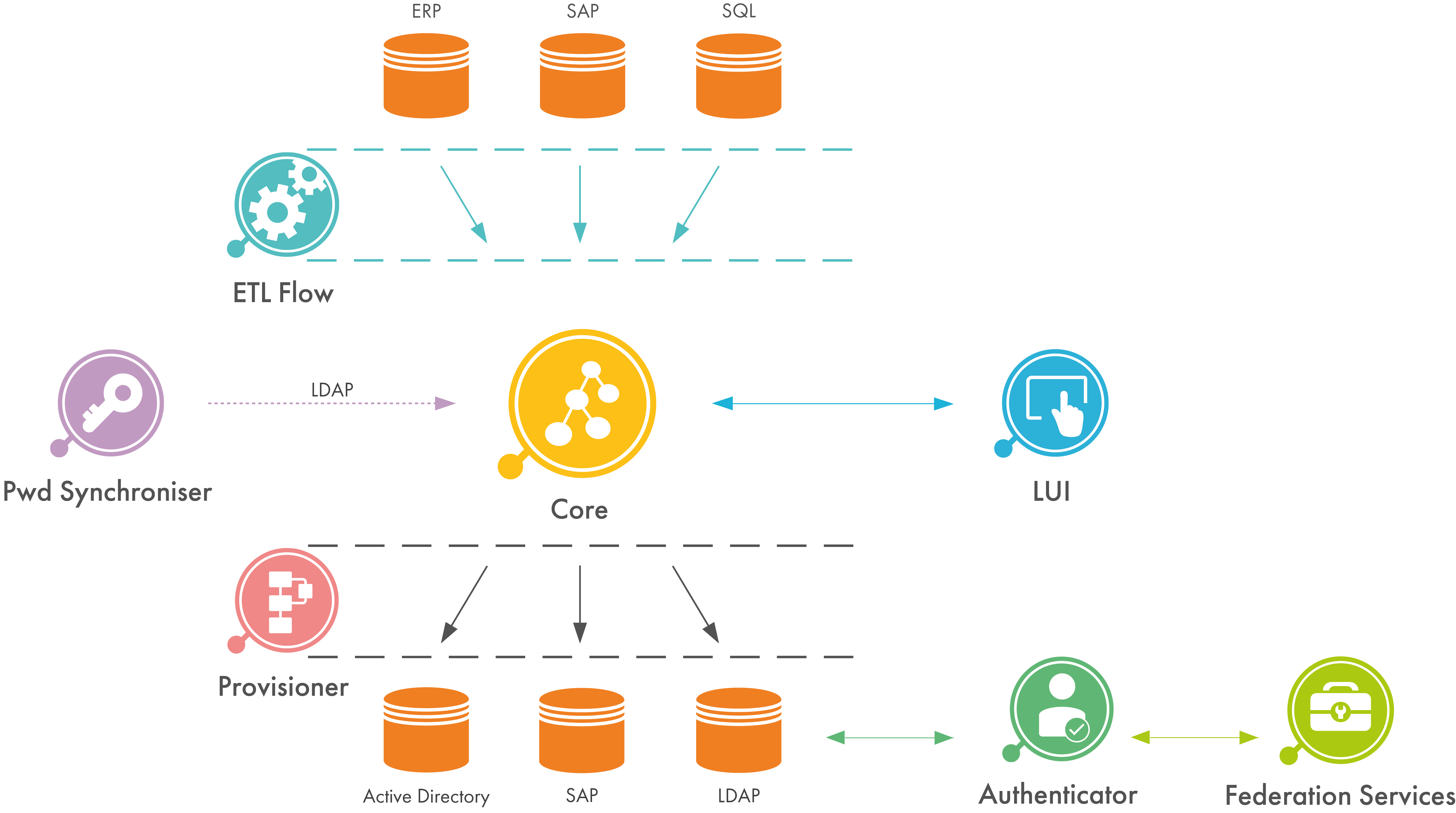
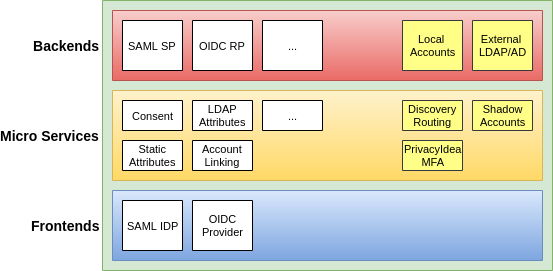
Within the didmos framework Authenticator is the central authentication component. However, it is possible to use Authenticator independently from didmos to secure any application. Authenticator is based on the open source software Satosa specifically adjusted to didmos.
The modular structure of SATOSA allows for attributes from different sources to be used. This makes it possible to use local accounts as well as common identity providers (IdP) such as the social networks Facebook and Twitter, any IdP of a SAML-based federation or other standard-compliant IdPs. The connection of such IdPs is easily configurable. This function is especially beneficial in federated Identity and Access Management (IAM). On the one hand, there are less accounts to be managed, on the other hand, users will have to remember only one password. Consequently, there will be less requests for the help-desk which will reduce costs in the long run due to the lowered administrative effort.